- Services

CloudPro Services
Our collaborative and innovative approach accelerates your deployments and dramatically improves your return on your IT investment.
Assess your network and web applications vulnerabilities
Let CloudPro make your transition to the cloud as seamless as possible.
Prepare your company to go to
market.Let us guide you with your cloud journey so you can focus on your business.
- Solutions
CloudPro Solutions
CloudPro provides world-class solutions from industry-leading cloud technology suppliers. - Industries

Industries
Out services are designed to meet the unique business needs of commercial verticals and indutries. - Company

Our Company
We deliver point and end-to-end solutions for industry leading IT companies. Our expertise, skill and commitment power your success.Our Mission
We provide world-class cloud consulting and engineering services to our customers and partners.
Teaming to Win
We provide world-class cloud consulting and engineering services to our customers and business partners.
Committed to Your Success
The uncompromising quality and dedication of our team of experts deliver bottom line results.
Diversity and Inclusion
We are committed to diversity and inclusion within the workplace and believe our differences make us better.
- Blog

Our Blog
Keep up-to-date with our current endeavours and outlook on the cloud.Articles
Let us guide you with your cloud migration so you can focus on your business.
Our Alliances
Keep up-to-date with our alliance activities and how they could be beneficial to your business.
- My CloudProKeep track of all of your CloudPro services, business communications and resources in one place.
Log In
Login to your MyCloudPro account to access your services and resources.
Create an Account
Register here to create a new MyCloudPro account.
Sales Support
Please let us know if you have any questions about our services.
Technical Support
Contact us for any technical support questions about our services.
- Support
Optimize
your Cloud
In collaboration with

Ensure you are getting the most from your cloud
To be successful with cloud implementations you must do regular health checks and optimize based on the results to continue health monitoring.
Reduce costs and optimize your cloud
Regular cloud health checks are essential to help you optimize your environment, maximize performance and resource utilization, and reduce costs.
At CloudPro, our team of cloud experts are focused on helping organizations accelerate their cloud transformation and get more out of their cloud investment.

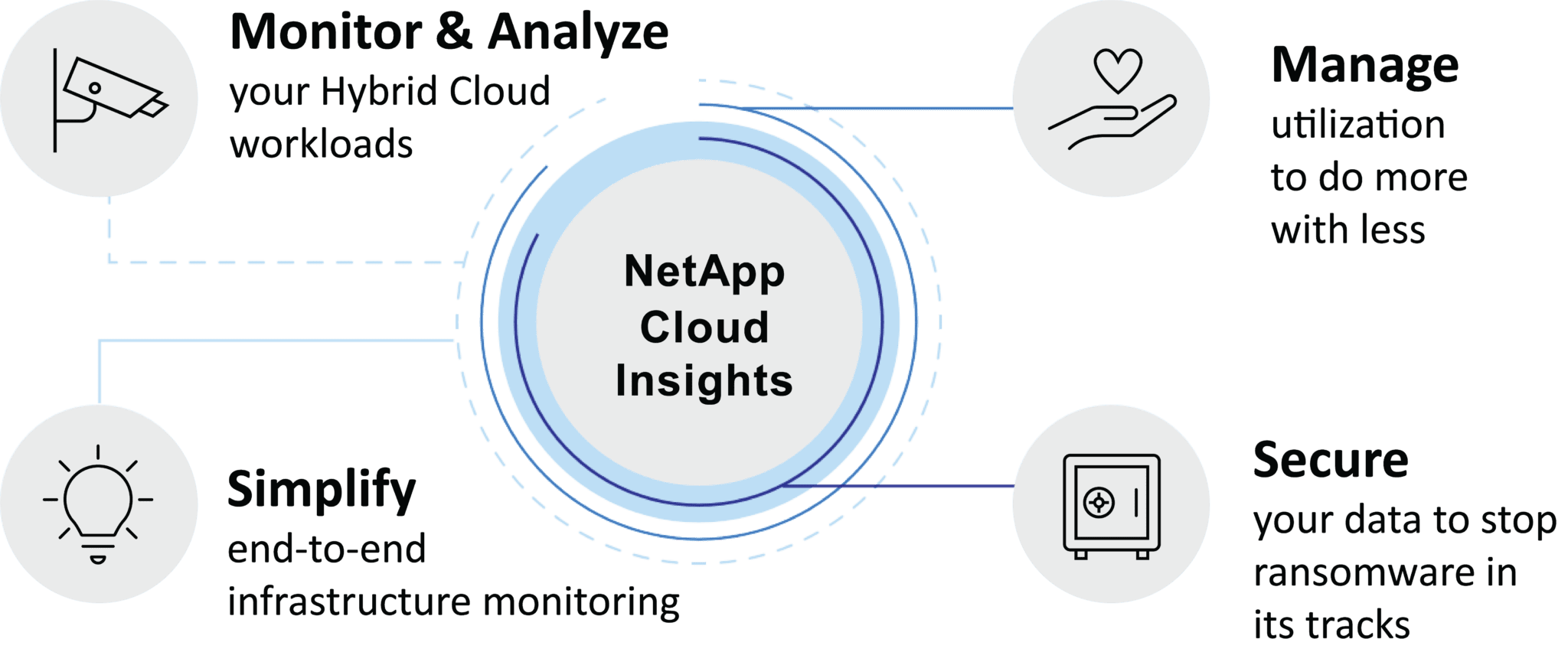
Get the most out of your cloud investment
CloudPro can help you reduce your overall cloud spend by identifying mismanaged resources and eliminating waste with Cloud Insights from NetApp.
Cloud Insights provides complete visibility into your infrastructure and applications. You can easily monitor, troubleshoot and optimize all your resources and applications across your entire technology stack, whether it’s on-prem or in the cloud.
Cloud Insights will help you:
- Find and fix problems faster
- Manage resources more effectively to do more with less
- Meet SLOs and SLAs during and after your move to cloud
- Detect ransomware before it impacts your business
Monitor, optimize and secure your cloud workloads
Cloud Insights can help you achieve greater efficiency and optimization both in the cloud and on-premises. You can configure Cloud Insights to identify areas of waste to reduce costs and optimize IT operations. Cloud Insights helps assess capacity and find performance issues 5x faster. Proactively reduce waste and maximize utilization to prevent performance bottlenecks.
Cloud Insights allows you to find and fix problems faster, manage resources more effectively and detect ransomware before it impacts your business.


Secure your data with Cloud Secure
Cloud Secure, a feature of NetApp Cloud Insights, analyzes data access patterns to identify ransomware risks. This powerful tool is invaluable in helping you discover potential attacks and protect your organization from critical data loss by detecting and stopping malicious activities.
Cloud Secure allows you to:
- Detect ransomware attacks before it’s too late
- Minimize the impact of an attack with automatic data backup and user restriction
- Gain visibility into malicious user activity and identify potential policy risks
- Satisfy audit reporting requirements, saving time and money
Maximize cost savings


Let CloudPro help you reduce costs and optimize your cloud
Optimize your cloud environment today!
See how CloudPro can help you reduce costs and optimize your cloud.




























